metemcyber
所属分类:以太坊
开发工具:Python
文件大小:1415KB
下载次数:0
上传日期:2022-01-31 00:53:41
上 传 者:
sh-1993
说明: 去中心化网络威胁情报改善框架
(Decentralized Cyber Threat Intelligence Kaizen Framework)
文件列表:
.dockerignore (14, 2022-01-13)
.readthedocs.yml (409, 2022-01-13)
LICENSE (11360, 2022-01-13)
MANIFEST.in (62, 2022-01-13)
Makefile (1719, 2022-01-13)
Pipfile (441, 2022-01-13)
Pipfile.lock (166038, 2022-01-13)
build.earth (1597, 2022-01-13)
contracts (0, 2022-01-13)
contracts\AddressGroup.sol (2874, 2022-01-13)
contracts\CTIBroker.sol (5741, 2022-01-13)
contracts\CTICatalog.sol (8671, 2022-01-13)
contracts\CTIOperator.sol (10190, 2022-01-13)
contracts\CTIToken.sol (1775, 2022-01-13)
contracts\MetemcyberMinimal.sol (876, 2022-01-13)
contracts\MetemcyberUtil.sol (5561, 2022-01-13)
contracts\Migrations.sol (371, 2022-01-13)
contracts\Votable.sol (3567, 2022-01-13)
docs (0, 2022-01-13)
docs\Makefile (720, 2022-01-13)
docs\conf.py (2154, 2022-01-13)
docs\cti (0, 2022-01-13)
docs\cti\actionable.rst (5531, 2022-01-13)
docs\cti\basic.rst (4340, 2022-01-13)
docs\cti\target.rst (8030, 2022-01-13)
docs\index.rst (1769, 2022-01-13)
docs\make.bat (795, 2022-01-13)
docs\requirements.txt (51, 2022-01-13)
docs\setup (0, 2022-01-13)
docs\setup\metemcyber.rst (5844, 2022-01-13)
docs\setup\misp.rst (2391, 2022-01-13)
gui (0, 2022-01-13)
gui\docker-path (14, 2022-01-13)
... ...
[](https://www.metemcyber.ntt.com)
# Metemcyber
> Decentralized Cyber Threat Intelligence Kaizen Framework. https://www.metemcyber.ntt.com
[](https://github.com/nttcom/metemcyber/actions/workflows/main.yml)
[](https://metemcyber.readthedocs.io/ja/latest/?badge=latest)

[](https://github.com/nttcom/metemcyber/discussions)
[](https://twitter.com/metemcyber)
**Pricom Mainnet (rpc.metemcyber.ntt.com)**
| Contract Name | Address |
| ---- | ---- |
| CTICatalog | 0xBcb4b84cdaB65C6e6Efe1697CC41a46D0AEaCA61 |
| CTIBroker | 0xC1814B834E1be7DeE7611fD5F747535369B8683e |
| CTIOperator | 0xd9CfB9276376C613e2f9A1691Ac694293b8c7ce8 |
| metemcyber_util(placeholder) | 0x0e5EECFF51a3ab2221fF6bBd240B20E8933ff28A\_\_$47ceb01e1c5513***bb2e8f2c8232f40551$\_\_ |
## ’ Overview
Metemcyber enables security collaboration and assessment all across the organization through the [intelligence cycle](https://en.wikipedia.org/wiki/Intelligence_cycle).
- “– [**Metemcyber User Documentation**](https://metemcyber.readthedocs.io/)
## ¨ Features
**Anyone can make a successful intelligence cycle.**
- Content-oriented Workflow
- Comparable Data Analysis Process
- Fault-tolerant Collaboration
- Disclosure Control of CTIs
- Measuring the Cost-Effectiveness of CTIs
- Transparency for Trust
- Monitoring the trading activity of CTIs
- Unlocking achievements based on your contribution.
- MISP-friendly ¤—
## … QuickStart
This exercise will be performed on the test environment.
```sh
apt install build-essential python3-dev
pip install -U pip
pip install -U 'metemcyber[cli]'
```
Check the current configuration:
```sh
metemctl config show
```
### ”‘ Create a new account
Create a new account if no keyfile available:
```sh
metemctl account create
```
Display your account details you are currently using:
```sh
metemctl account show
```
> **You must agree to [the terms of service](https://forms.office.com/Pages/ResponsePage.aspx?id=Mu8pprpnpkeOs-xDk1ZE_FdfnH75qvpDtqTkNo9NCzRUN1hRM1lIVVZCTUU3V1VJVjhFWEtQSDFMNy4u).** This is an experimental project on the enterprise ethereum of NTT Communications. **You will get a promo code if you agree to these terms.**
Get a promo code via email, and airdrop yourself some ETH to get started:
```sh
metemctl account airdrop $PROMOTE_CODE_IN_THE_CONFIRMATION_MAIL
```
### ’ Collect CTIs
Search for the CTI token you want to buy (e.g. OSINT)
```sh
metemctl ix search 'OSINT'
```
Enter the index number of the CTI token to be purchased. The CTI token address can also be accepted.
```sh
metemctl ix buy $TOKEN_INDEX_OR_ADDRESS
```
> If you don't have a global IP address or can't traverse a firewall or NAT, **you need an account to use [ngrok](https://dashboard.ngrok.com/).** [Setup a local ngrok environment](https://dashboard.ngrok.com/get-started/setup).
>Download [ngrok](https://dashboard.ngrok.com/) and extract it.
>Open the application directory to **put the ngrok executable file there**:
>```sh
>metemctl open-app-dir
>```
>```sh
>$ ls "$(metemctl open-app-dir --print-only)"
>external-links.json metemctl.ini ngrok ...
>```
>**Ngrok need to connect your ngrok account.** Make sure the ngrok *authtoken* exists after [ngrok setup](https://dashboard.ngrok.com/get-started/setup):
>```sh
>cat ~/.ngrok2/ngrok.yml
>```
>Change the configurations so that the daemon to receive data uses ngrok (from 0 to 1):
>```sh
>metemctl config edit
>...
>[seeker]
>...
>ngrok = 1
Start a seeker daemon to receive data.
```sh
metemctl seeker start
metemctl seeker status
```
Use the CTI token to receive MISP objects at the configured public IP/URL.
```sh
metemctl ix use $TOKEN_INDEX_OR_ADDRESS
```
> If you want to use **specific IP/URL**, you need to tell the Solver daemon your global IP/URL and port number:
>```sh
>metemctl ix use --seeker http(s)://$ADDR:$PORT $TOKEN_INDEX_OR_ADDRESS
>```
## Run the Intelligence Cycle
In this section, you will run the intelligence cycle using the exercise *ir-exercise* for Incident Response.
> **You need to enable the test catalog as primary catalog**.
>Enable the test catalog & Disable the production catalog:
>```sh
>metemctl ix catalog enable 0x168DD95472cEaF5c28447C8b07A593e205E92A12 # test
>metemctl ix catalog disable 0xBcb4b84cdaB65C6e6Efe1697CC41a46D0AEaCA61 # production
>```
>Check your catalog settings:
>```sh
>$ metemctl ix catalog show
>Catalogs *:active
> *1 0x168DD95472cEaF5c28447C8b07A593e205E92A12 # test
> 2 0xBcb4b84cdaB65C6e6Efe1697CC41a46D0AEaCA61 # production
>```
### ¤– Create a new workflow
Metemcyber can be used not only for CTI dissemination but also CTI creation.
```sh
metemctl new--starter=ir-exercise
```
Implement the analysis process into your workflow by selecting the event ID (In many cases, the same as the UUID of MISP object), the category of CTI (Fraud, Incident Response, Risk Analysis, Security Operations, Security Leadership, Vulnerability Management), and the content(IOCs, TTPs, etc.) you want to include in the CTI.
This is an important piece of evidence to check the "Direction" step in the intelligence cycle.
```sh
Select Intelligence Category (Fraud, IR, RA, SecOps, SecLead, Vuln) [IR]:
Input a new event_id(UUID) [70be8ba5-fa7f-4b8e-aa04-dc76e0fa8c42]:
0: IOC
1: TTP
2: Workflow
Choose contents to be include [0,1]:
================================================================
Event ID: 70be8ba5-fa7f-4b8e-aa04-dc76e0fa8c42
Category: Incident Response
Contents: ['TTPs', 'IOCs']
================================================================
Are you sure you want to create it? [y/N]:
```
### “ Summarize the data analysis process
> **Make sure Seeker is running** to receive the data.
>
>```sh
>metemctl seeker status
>```
You need to use [Kedro](https://github.com/quantumblacklabs/kedro) to summarize your data analysis process into a workflow.
In practice, it is difficult to clearly separate the steps of "Collection", "Processing" and "Analysis" in the intelligence cycle, which makes the data analysis process look complicated.
Please keep the following two points to make the data analysis process more maintainable.
- Using the Kedro pipeline to describe *Analysis Strategy*
- Using the Kedro nodes to describe *Analysis Method*
These are important pieces of evidence to check the "Processing" and "Analysis" step in the intelligence cycle.
**For the success of the intelligence cycle, we are more focused on evaluating the data analysis process than on automating the CTI consumption process.**
Get data for the exercise *ir-exercise*:
```sh
metemctl ix search '[ir-exercise]'
metemctl ix buy $TOKEN_INDEX_OR_ADDRESS
metemctl ix use $TOKEN_INDEX_OR_ADDRESS
metemctl ix extract $TOKEN_INDEX_OR_ADDRESS
```
Run the ir-exercise workflow:
```sh
metemctl run --setup
```
Check the contents of your CTI product and the workflow:
```sh
metemctl check --viz
```
The `--viz` option allows you to visualize your data analysis process described by the workflow. (the same as `kedro viz`)
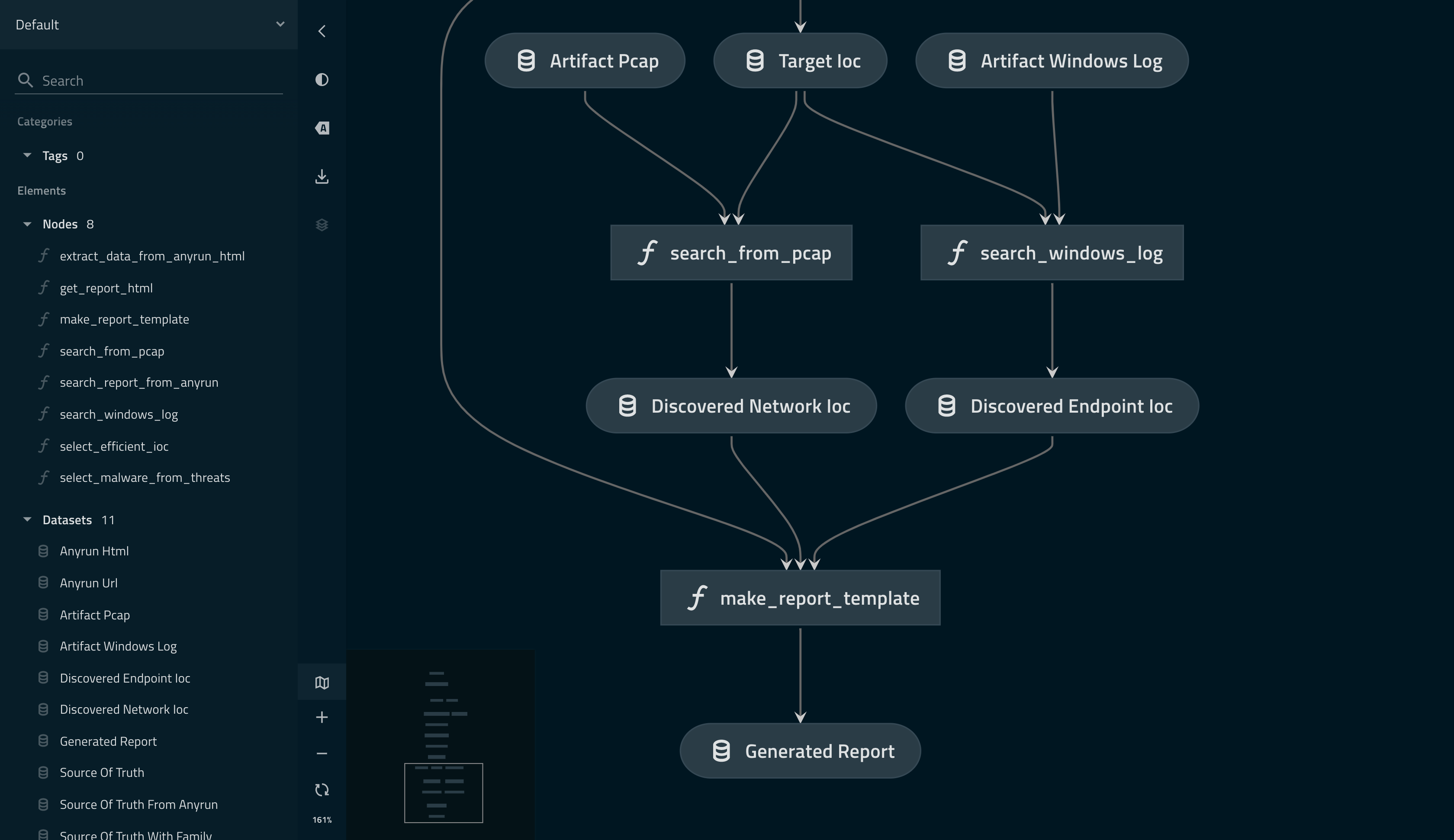
### Disseminate your CTI products to everyone:
> ***Solver* must be running** to send the data to token holders.
>
>```sh
>metemctl solver start --enable
>```
>MISP objects can be distributed when Solver is working properly.
>```sh
>$ metemctl solver status
>Solver running with operator you configured(0xe889b84a209719B8f0272376dB49946DbD177aE6).
>```
```sh
metemctl publish
```
‰‰‰ Welcome to Metemcyber! ‰‰‰
## “– Documentation
For more information see the [documentation](https://metemcyber.readthedocs.io/).
## – LICENSE
```
Copyright 2021 NTT Communications Corporation
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
```
近期下载者:
相关文件:
收藏者: