the-riot-protocol
说明: 使用防暴协议增强物联网网络安全。它提供设备身份验证、数据加密、去中心化...
(Enhance IoT network security with the Riot Protocol. It offers device authentication, data encryption, decentralized key generation, and blockchain- based authentication for secure and reliable communication between devices and users.)
(Enhance IoT network security with the Riot Protocol. It offers device authentication, data encryption, decentralized key generation, and blockchain- based authentication for secure and reliable communication between devices and users.)
文件列表:
.vscode (0, 2023-07-05)
.vscode\launch.json (523, 2023-07-05)
client (0, 2023-07-05)
client\.env.local.example (84, 2023-07-05)
client\.prettierignore (40, 2023-07-05)
client\.prettierrc.json (67, 2023-07-05)
client\CODING_STYLE.md (164, 2023-07-05)
client\CONTRIBUTING.md (1194, 2023-07-05)
client\next.config.js (212, 2023-07-05)
client\package-lock.json (841026, 2023-07-05)
client\package.json (1725, 2023-07-05)
client\postcss.config.js (82, 2023-07-05)
client\public (0, 2023-07-05)
client\public\Moralis-DarkBG.svg (8116, 2023-07-05)
client\public\Moralis-LightBG.svg (6249, 2023-07-05)
client\public\android-chrome-192x192.png (12405, 2023-07-05)
client\public\android-chrome-512x512.png (43493, 2023-07-05)
client\public\apple-touch-icon.png (11375, 2023-07-05)
client\public\ethereum.png (90848, 2023-07-05)
client\public\favicon-16x16.png (660, 2023-07-05)
client\public\favicon-32x32.png (1546, 2023-07-05)
client\public\favicon.ico (15406, 2023-07-05)
client\public\ganache.png (6634, 2023-07-05)
client\public\gnosis.png (3378, 2023-07-05)
client\public\luniverse.jpg (9689, 2023-07-05)
client\public\polygon.png (2750, 2023-07-05)
client\public\riot.png (114656, 2023-07-05)
client\public\site.webmanifest (263, 2023-07-05)
... ...
.vscode\launch.json (523, 2023-07-05)
client (0, 2023-07-05)
client\.env.local.example (84, 2023-07-05)
client\.prettierignore (40, 2023-07-05)
client\.prettierrc.json (67, 2023-07-05)
client\CODING_STYLE.md (164, 2023-07-05)
client\CONTRIBUTING.md (1194, 2023-07-05)
client\next.config.js (212, 2023-07-05)
client\package-lock.json (841026, 2023-07-05)
client\package.json (1725, 2023-07-05)
client\postcss.config.js (82, 2023-07-05)
client\public (0, 2023-07-05)
client\public\Moralis-DarkBG.svg (8116, 2023-07-05)
client\public\Moralis-LightBG.svg (6249, 2023-07-05)
client\public\android-chrome-192x192.png (12405, 2023-07-05)
client\public\android-chrome-512x512.png (43493, 2023-07-05)
client\public\apple-touch-icon.png (11375, 2023-07-05)
client\public\ethereum.png (90848, 2023-07-05)
client\public\favicon-16x16.png (660, 2023-07-05)
client\public\favicon-32x32.png (1546, 2023-07-05)
client\public\favicon.ico (15406, 2023-07-05)
client\public\ganache.png (6634, 2023-07-05)
client\public\gnosis.png (3378, 2023-07-05)
client\public\luniverse.jpg (9689, 2023-07-05)
client\public\polygon.png (2750, 2023-07-05)
client\public\riot.png (114656, 2023-07-05)
client\public\site.webmanifest (263, 2023-07-05)
... ...
# THE RIOT PROTOCOL: A Decentralized IOT Security Gateway
----
### The Problem
IoT is facing identity, security, and interoperability problems. Current systems rely on a centralized client-server model that will soon be unsatisfactory due to the rapid increase in the number of devices connected to the Internet.
Networks are highly prone to trojan devices that piggyback into the so-called smart devices and steal sensitive data and hack into our lives. This is more cynical when it comes to industrial automation, where high-volume sensor data can easily get into the wrong hands.
A single protocol that ensures device authentication, authorization and manages the data layer is a much needed technology of the hour.

### What is RioT?
The Internet of Things (IoT) has seen widespread adoption in recent years, connecting numerous devices to the internet. However, current IoT networks are vulnerable to various security threats such as data breaches, unauthorized access, and cyber-attacks. To address these security challenges, we propose the Riot protocol - a comprehensive solution for securing IoT networks by providing device authentication, data encryption, decentralized key generation, scalability, and more with cryptographic wallet-based authentication. This protocol ensures the confidentiality, integrity, and authenticity of the data exchanged between IoT devices (publishers) or users (subscribers). The Riot protocol aims to provide a secure and reliable communication between devices, offering an extensive solution to the challenges of IoT security using blockchain technology.
The Riot protocol provides robust device authentication and data encryption mechanisms to secure the communication between IoT devices and users.
With decentralized key generation, the Riot protocol ensures that cryptographic keys are generated securely and distributed in a decentralized manner.
#### Authentication & Encryption:
The Riot protocol provides robust device authentication and data encryption mechanisms to secure the communication between IoT devices and users.
 #### Decentralized Key Generation
With decentralized key generation, the Riot protocol ensures that cryptographic keys are generated securely and distributed in a decentralized manner.
#### Decentralized Key Generation
With decentralized key generation, the Riot protocol ensures that cryptographic keys are generated securely and distributed in a decentralized manner.
 ## Technical Implementation
The platform has a cross-chain infrastructure that lets you secure devices on two of the most scalable chains available right now: One on PolygonzkEVM and the other on PolygonPOS.

#### Modules
- Blockchain Smart Contract:
The Blockchain Smart Contract module is responsible for managing the group membership, verifying device identities, and storing device keys. The module uses Ethereum smart contracts to enforce the rules and regulations of the protocol. When a new device is registered in the system, the smart contract verifies its identity and adds it to the group. The device keys are also stored in the smart contract, making them easily accessible to other devices in the group.
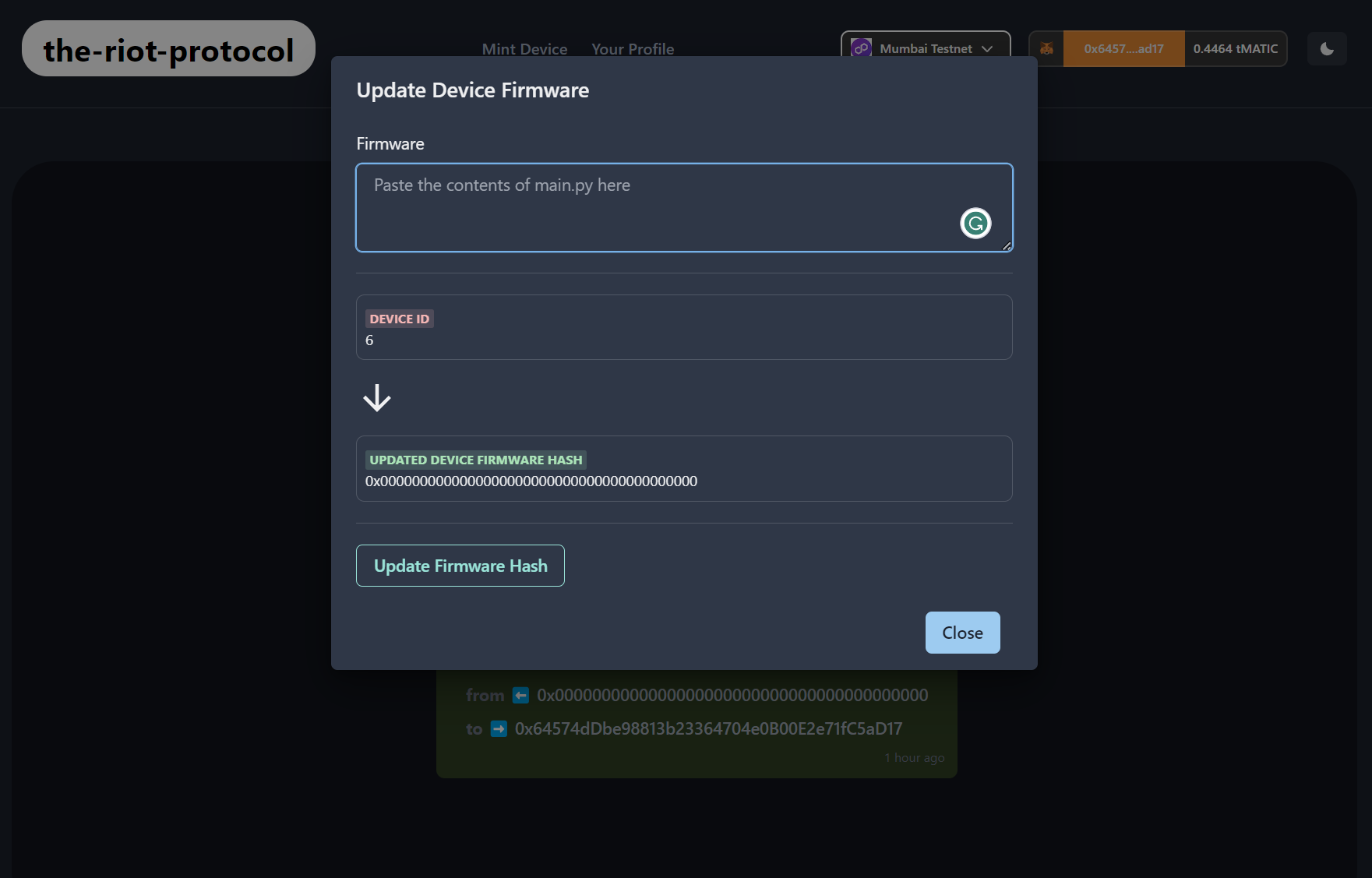
- Device firmware module:
The Device Firmware Module is responsible for managing the firmware of each device in the Riot protocol. It ensures that all devices are running the latest firmware and are compatible with the other devices in the group. The module uses Over-the-Air (OTA) updates to remotely update the firmware of devices in the group. It also checks the integrity of the firmware by comparing its hash with the hash stored in the blockchain network.
- Key Distribution Module:
The Key Distribution Module in the Riot protocol is responsible for generating and distributing unique device keys to authorized devices. The keys are used to encrypt and decrypt messages sent between devices in a group. The module uses a combination of group salt, session salt, and other token ingredients to create a Merkle hash, which is used to generate a unique key for each device. These keys are then securely distributed to each device in the group using the blockchain network.
- Device Registration Module:
The Device Registration Module is responsible for registering new devices in the Riot protocol. It verifies the identity of the device by checking its firmware hash and device subscriber address. Once the identity is verified, the module generates a unique device ID and adds the device to the blockchain network. The module also generates a unique device key for the device using the Key Distribution Module.
- Encryption/Decryption Module:
The encryption/decryption module is responsible for securing the IoT sensor data before it is stored in the data storage microservice. Fernet symmetric encryption is used for encryption, which provides a high level of security and speed.
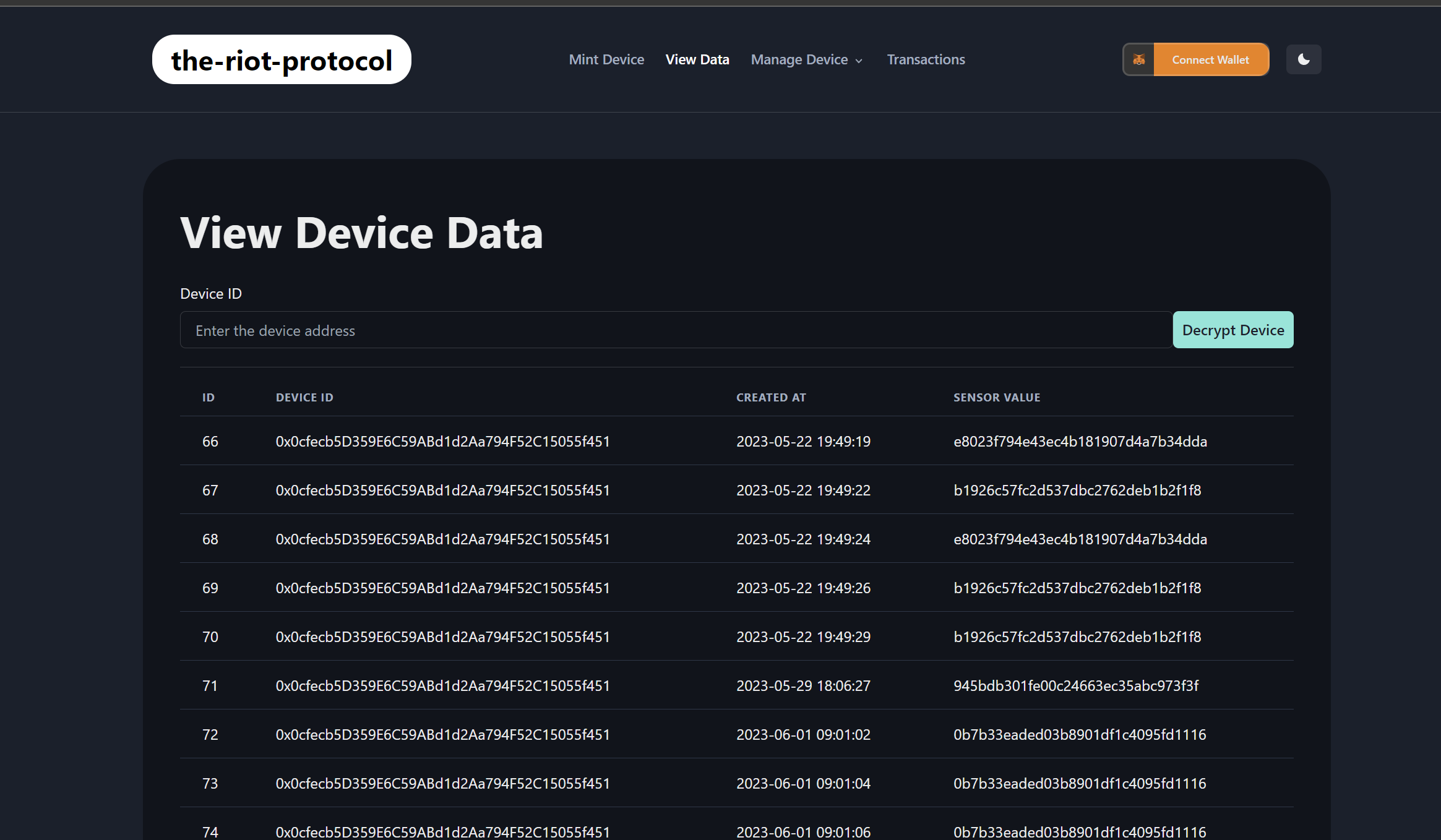
### Screenshots
## Technical Implementation
The platform has a cross-chain infrastructure that lets you secure devices on two of the most scalable chains available right now: One on PolygonzkEVM and the other on PolygonPOS.

#### Modules
- Blockchain Smart Contract:
The Blockchain Smart Contract module is responsible for managing the group membership, verifying device identities, and storing device keys. The module uses Ethereum smart contracts to enforce the rules and regulations of the protocol. When a new device is registered in the system, the smart contract verifies its identity and adds it to the group. The device keys are also stored in the smart contract, making them easily accessible to other devices in the group.
- Device firmware module:
The Device Firmware Module is responsible for managing the firmware of each device in the Riot protocol. It ensures that all devices are running the latest firmware and are compatible with the other devices in the group. The module uses Over-the-Air (OTA) updates to remotely update the firmware of devices in the group. It also checks the integrity of the firmware by comparing its hash with the hash stored in the blockchain network.
- Key Distribution Module:
The Key Distribution Module in the Riot protocol is responsible for generating and distributing unique device keys to authorized devices. The keys are used to encrypt and decrypt messages sent between devices in a group. The module uses a combination of group salt, session salt, and other token ingredients to create a Merkle hash, which is used to generate a unique key for each device. These keys are then securely distributed to each device in the group using the blockchain network.
- Device Registration Module:
The Device Registration Module is responsible for registering new devices in the Riot protocol. It verifies the identity of the device by checking its firmware hash and device subscriber address. Once the identity is verified, the module generates a unique device ID and adds the device to the blockchain network. The module also generates a unique device key for the device using the Key Distribution Module.
- Encryption/Decryption Module:
The encryption/decryption module is responsible for securing the IoT sensor data before it is stored in the data storage microservice. Fernet symmetric encryption is used for encryption, which provides a high level of security and speed.
### Screenshots
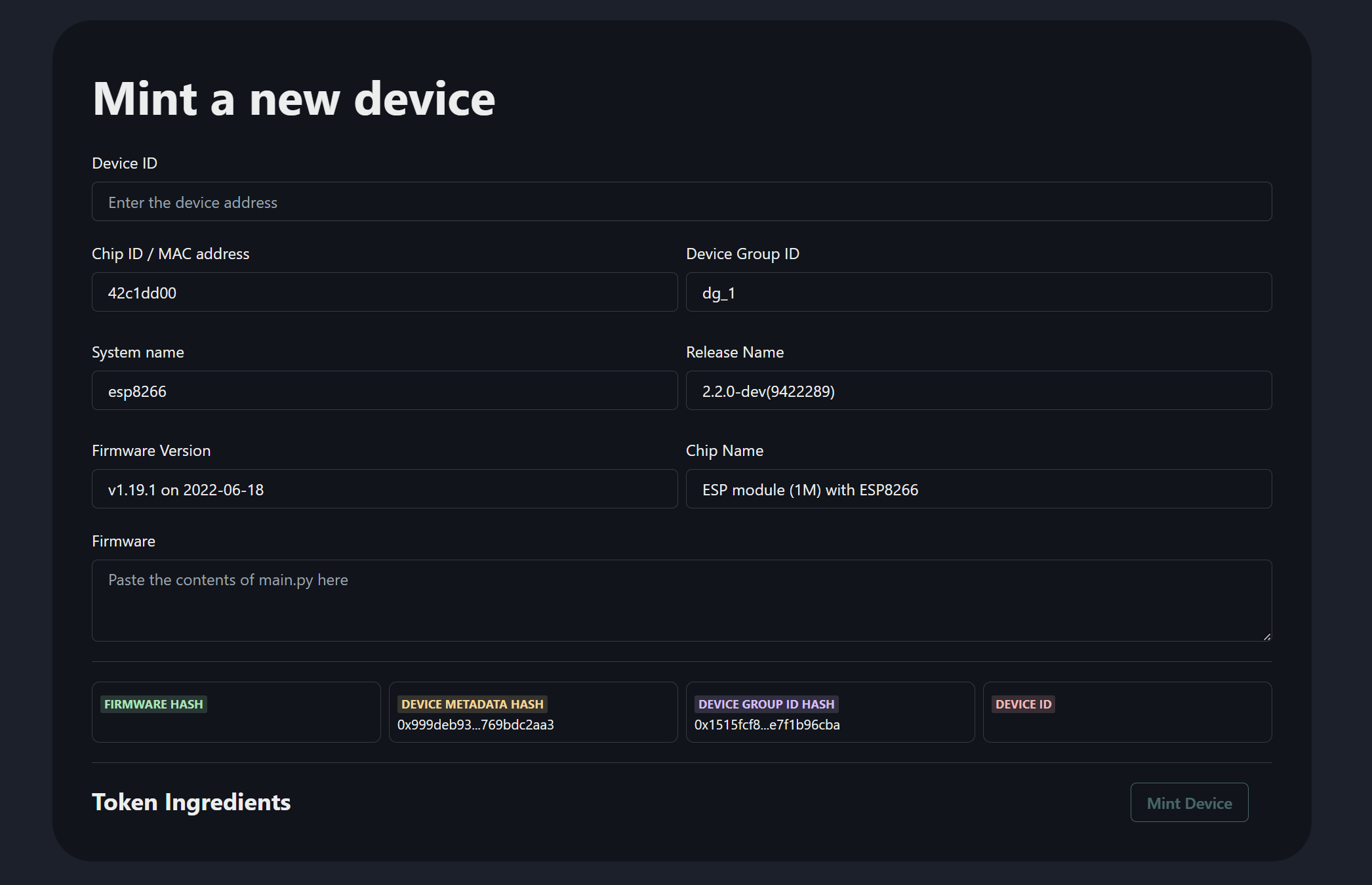
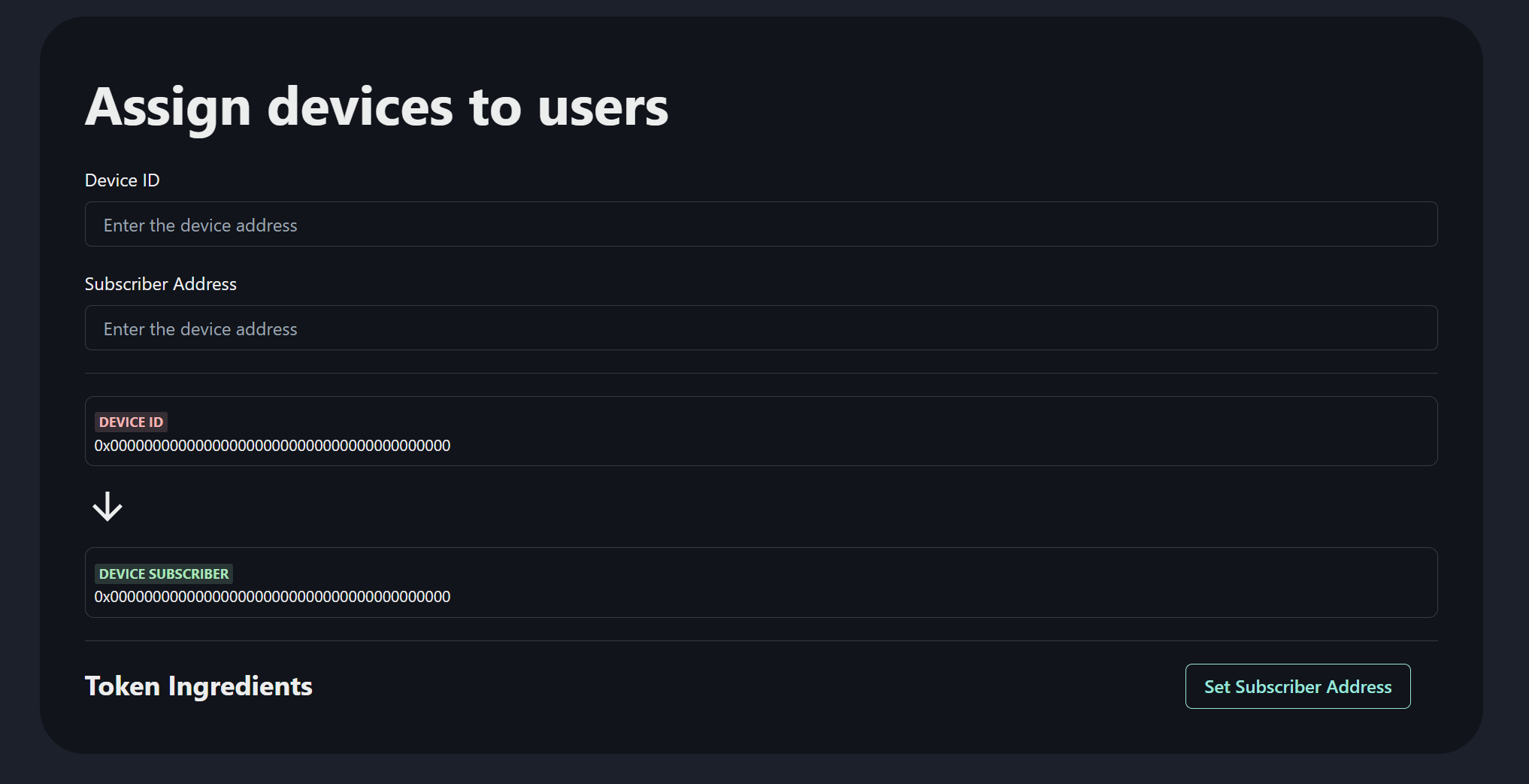
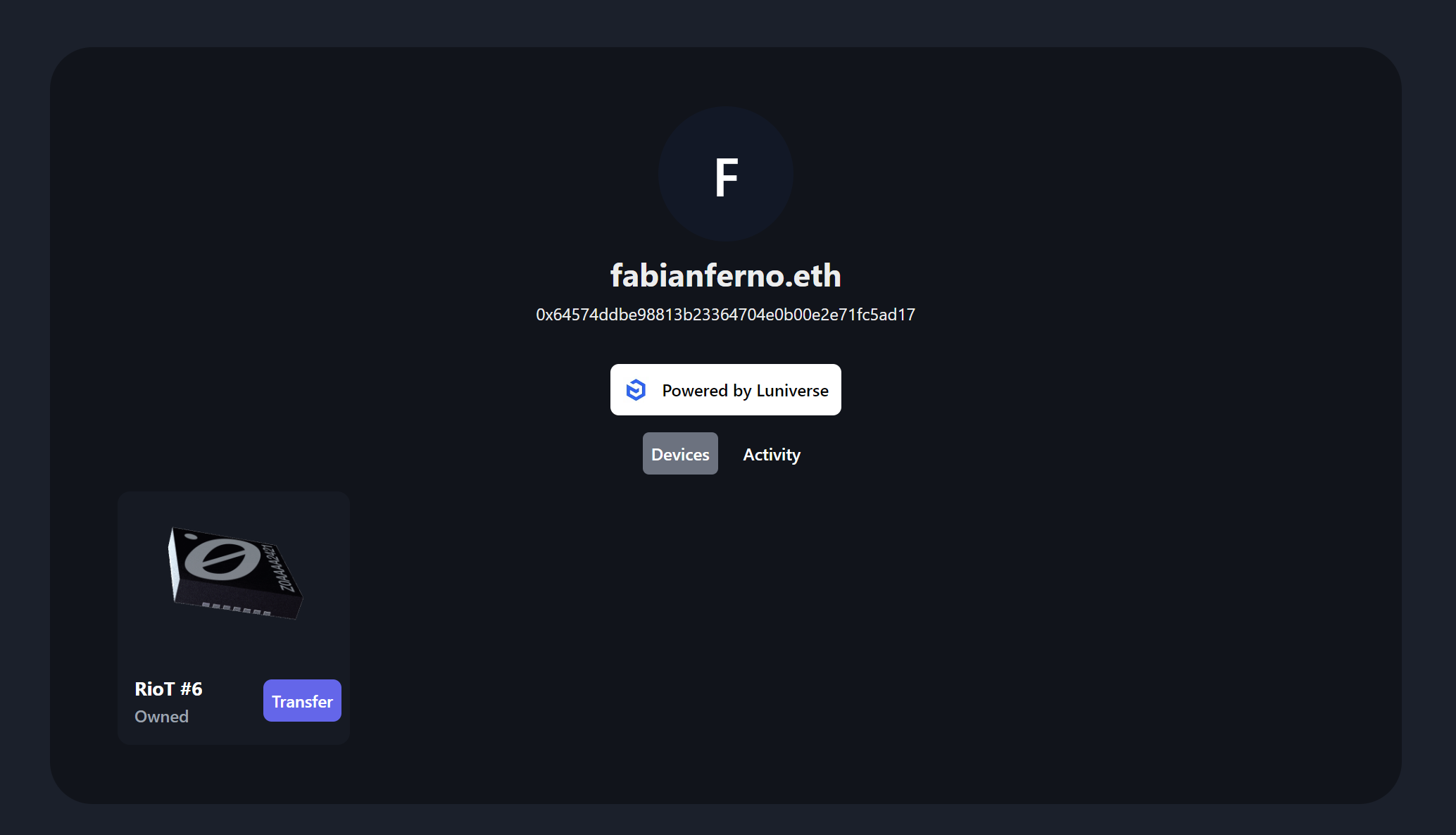


 ### Tracks applied
- Application Layer Track
- Tooling & Public Goods Track
- zkEVM Tooling Track
- Specific Problem Statements Track: (Open Track)
- Newman Capital
- Luniverse (Luniverse NOVA's multichain API)
#### BUIDLERS
- @fabianferno
- @gabrielaxyeth
### Tracks applied
- Application Layer Track
- Tooling & Public Goods Track
- zkEVM Tooling Track
- Specific Problem Statements Track: (Open Track)
- Newman Capital
- Luniverse (Luniverse NOVA's multichain API)
#### BUIDLERS
- @fabianferno
- @gabrielaxyeth
近期下载者:
相关文件:
收藏者: