Red-Terroir
说明: 用于构建HTTP、DNS、钓鱼和邮件服务器红队基础架构的地形资源,
(Terraform resources for building HTTP, DNS, phishing, and mail server red team infrastructure,)
(Terraform resources for building HTTP, DNS, phishing, and mail server red team infrastructure,)
文件列表:
data/ (0, 2019-06-19)
data/apache/ (0, 2019-06-19)
data/apache/000-default.conf (1448, 2019-06-19)
data/apache/default-ssl.conf (6189, 2019-06-19)
data/apache/htaccess (2204, 2019-06-19)
data/images/ (0, 2019-06-19)
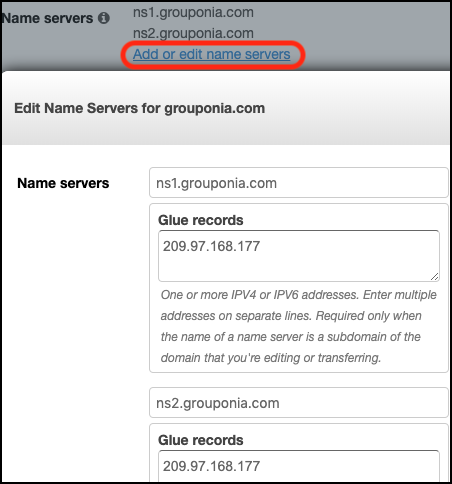
data/images/glue_records.png (41828, 2019-06-19)
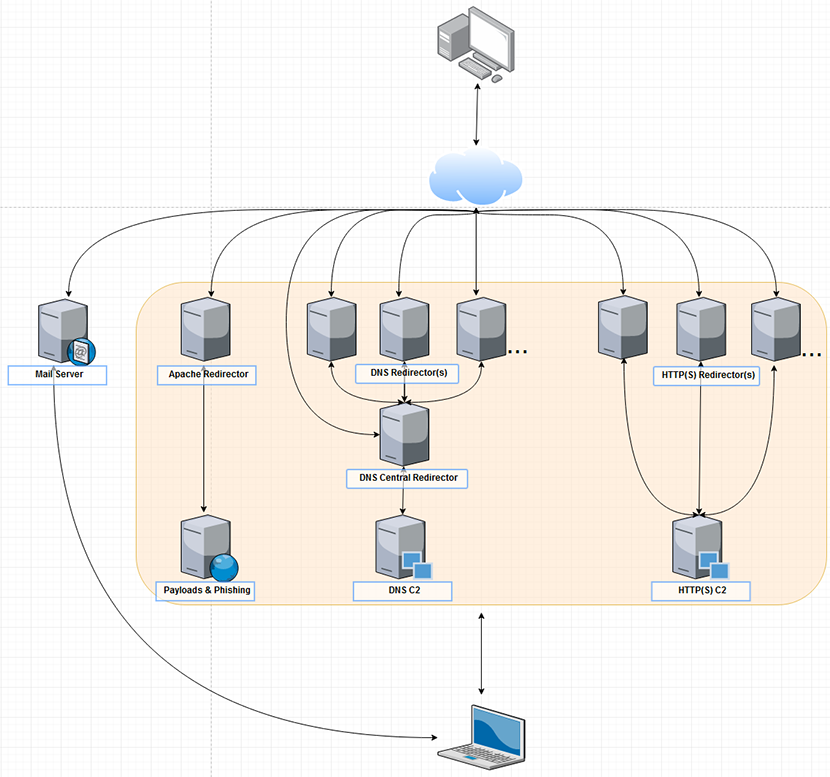
data/images/infrastructure_diagram.png (176140, 2019-06-19)
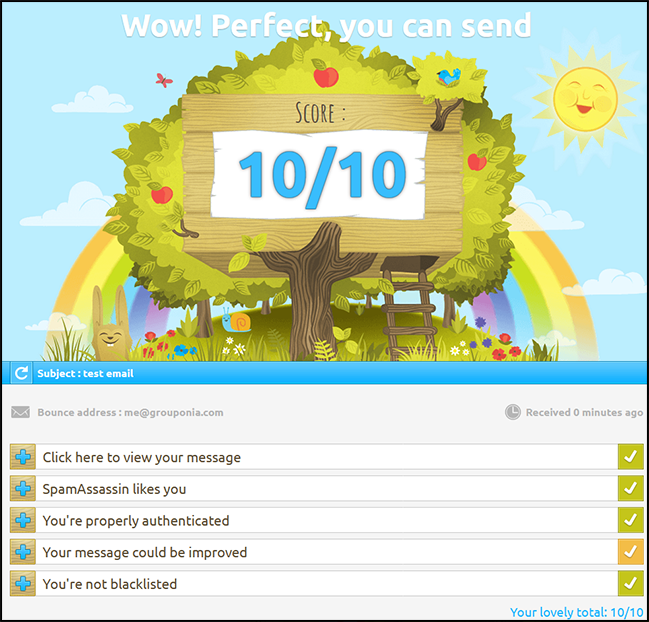
data/images/mail-tester.png (314059, 2019-06-19)
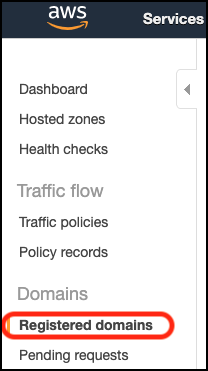
data/images/registered_domains.png (19869, 2019-06-19)
data/scripts/ (0, 2019-06-19)
data/scripts/apt_update.sh (110, 2019-06-19)
data/scripts/beef.sh (271, 2019-06-19)
data/scripts/cobalt_strike.sh (460, 2019-06-19)
data/scripts/gophish.sh (285, 2019-06-19)
data/scripts/lets_encrypt.sh (1888, 2019-06-19)
data/scripts/metasploit.sh (234, 2019-06-19)
data/scripts/mod_rewrite.sh (1499, 2019-06-19)
data/ssh/ (0, 2019-06-19)
digitalocean_firewall.tf (1596, 2019-06-19)
local-only-resources.tf (717, 2019-06-19)
main.tf (13728, 2019-06-19)
outputs.tf (1485, 2019-06-19)
providers.tf (180, 2019-06-19)
security-groups.tf (6366, 2019-06-19)
terraform.tfvars (407, 2019-06-19)
variables.tf (379, 2019-06-19)
vpc.tf (585, 2019-06-19)
data/apache/ (0, 2019-06-19)
data/apache/000-default.conf (1448, 2019-06-19)
data/apache/default-ssl.conf (6189, 2019-06-19)
data/apache/htaccess (2204, 2019-06-19)
data/images/ (0, 2019-06-19)
data/images/glue_records.png (41828, 2019-06-19)
data/images/infrastructure_diagram.png (176140, 2019-06-19)
data/images/mail-tester.png (314059, 2019-06-19)
data/images/registered_domains.png (19869, 2019-06-19)
data/scripts/ (0, 2019-06-19)
data/scripts/apt_update.sh (110, 2019-06-19)
data/scripts/beef.sh (271, 2019-06-19)
data/scripts/cobalt_strike.sh (460, 2019-06-19)
data/scripts/gophish.sh (285, 2019-06-19)
data/scripts/lets_encrypt.sh (1888, 2019-06-19)
data/scripts/metasploit.sh (234, 2019-06-19)
data/scripts/mod_rewrite.sh (1499, 2019-06-19)
data/ssh/ (0, 2019-06-19)
digitalocean_firewall.tf (1596, 2019-06-19)
local-only-resources.tf (717, 2019-06-19)
main.tf (13728, 2019-06-19)
outputs.tf (1485, 2019-06-19)
providers.tf (180, 2019-06-19)
security-groups.tf (6366, 2019-06-19)
terraform.tfvars (407, 2019-06-19)
variables.tf (379, 2019-06-19)
vpc.tf (585, 2019-06-19)
# Red Terroir
近期下载者:
相关文件:
收藏者: